RULES & TERMS
This document answers frequently asked questions about bounty programs and explains the submission and confidentiality requirements of the programs.
The decisions made by 360 Security Response Center (360SRC) are final and binding. 360SRC may cancel this program at any time, for any reason. Be sure to read all of these terms before sending us any submission. If you send us a submission for this program, you are agreeing to these terms. If you do not want to agree with these terms, do not send us any submissions or otherwise participate in this program.
HOW DO I SUBMIT A VULNERABILITY REPORT FOR BOUNTY?
Send your complete submission to 360SRC (including instructions to reproduce the vulnerability) at security@360.cn.com.
An important note:
360SRC will exercise reasonable efforts to clarify indecipherable or incomplete submissions, but more complete submissions are often eligible for higher bounties.
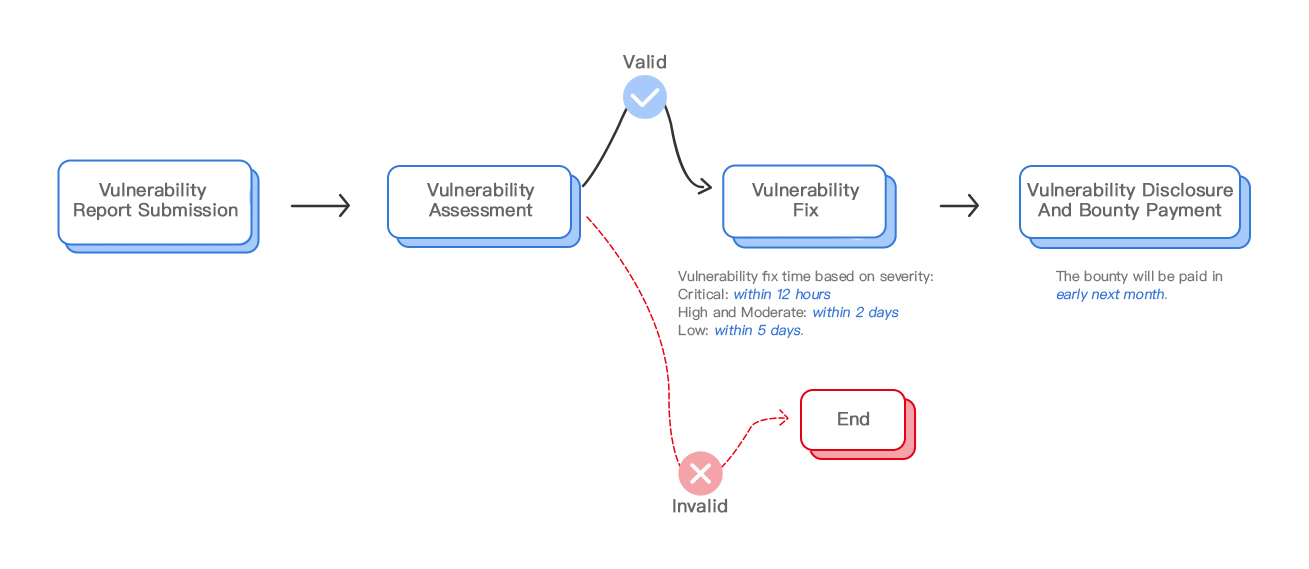
WHAT HAPPENS AFTER I SUBMIT THE REPORT?
You will receive an email stating that we have received your submission.
Our engineers will review the submission and validate the vulnerability. The review time will vary depending on the complexity and completeness of your submission, as well as on the number of submissions we receive.
After your submission has been validated, we will contact you to process your payment.
HOW DOES 360SRC DETERMINE BOUNTY PAYMENTS?
360SRC retains sole discretion in determining which submissions are qualified, according to the rules of each program.
If we receive multiple bug reports for the same issue from different parties, the bounty will be granted to the first eligible submission.
If a duplicate report provides new information that was previously unknown to 360SRC, we will award a differential to the person submitting the duplicate report.
WHAT CAN I DISCLOSE ABOUT A VULNERABILITY REPORT I SUBMITTED FOR BOUNTY AND WHEN CAN I DISCLOSE IT?
If you report a vulnerability, you are agreeing that you will never disclose functioning exploit code (including binaries of that code) for the applicable vulnerability to any other entity, unless 360SRC makes that code generally publicly available or you are required by law to disclose it.
Please do not discuss the vulnerability in any form prior to 360SRC notifying you that it is fixed. Disclosing a vulnerability before we notify you that it has been fixed may render you ineligible to participate in any bounty programs.
Please contact security@360.cn if you intend to discuss the vulnerability after it has been fixed. This includes blog posts, public presentations, whitepapers and other media. We’re happy to advertise your public talk here.
CAN I SUBMIT A VULNERABILITY WHEN I FIND IT AND A WORKING EXPLOIT LATER?
Yes. We want to know about a security vulnerability as soon as you’ve found it. We will award you the bounty for the vulnerability reported. If you give us the functioning exploit within 90 days of submitting the vulnerability, we will top it off and pay you the entire bounty amount.
CVEs ID SCOPE:
360 Safe Router[only router's firmware vulnerability, the web vulnerabilities in router's administration page is not included]
CVEs are an industry standard for uniquely identifying vulnerabilities. To avoid confusion, it’s important that the first public mention of a vulnerability should include a CVE. For vulnerabilities that go past deadline, we ensure that a CVE has been pre-assigned.
Low severity issues are generally addressed in the next major versions, instead of through our Monthly Security Bulletins, and we will generally not assign CVEs for this severity level.
How to publish the vulnerability information?
After the bug is fixed, we will issue a security advisory on the website. and what problems have been fixed in the latest software release.